We all see the headlines these days with alarming frequency: cyberattacks against companies in all industries are occurring in greater numbers and with increasing severity. For financial services professionals, the threat is acute. Financial services organizations encounter security incidents three times more frequently than organizations in other industries and the total cost incurred by cybercrime is higher for financial services companies than any other sector. Independent investment advisors have largely escaped the devastating, headline-grabbing attacks other companies have faced—such as Target or Visa. However, regulators are focusing in more than ever to be sure that firms are implementing safeguards to ensure investors are protected.
Recent guidance from the Securities Exchange Commission (SEC) and Financial Industries Regulatory Authority (Finra) indicate that written information security policies and strong governance from firm management are essential. Whether mandated or not, a solid cybersecurity program is critical to mitigate cybercrime and fraud attacks. It will also help safeguard your brand and maintain confidence among your clients.
Cybersecurity planning is complex and multi-faceted. To be effective, plans must reflect a firm’s unique business practices, its procedures and its technology platforms. The planning process must also be fully supported by firm leadership and involve collaboration among appropriate stakeholders.
Yet as daunting as it can seem, there are proven structures for cybersecurity planning that can guide the process. Finra and the SEC each recommend—encourage, in fact—the use of basic standardized frameworks to get started. The National Institute of Standards and Technology (NIST) framework is one such structure firms can leverage to formulate a plan that will reflect unique areas of risk.
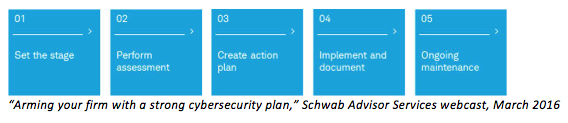
Exploring the planning process for the first time can be challenging given the volume of information available to advisors from the NIST alone. But there are essentially three key elements of the NIST framework. Understanding the basics of each is a good place to start.
Phase I: Taking Stock
The foundation of the NIST approach is the framework core, which involves taking a comprehensive inventory of assets that must be safeguarded, along with existing controls that protect them. The inventory should include a firm’s hardware, software, data and intellectual property, and client information. It should also involve “directional” inventory, which includes firm-wide business strategy and future technological needs. The inventory should then be ranked by importance.
Next, identify risks associated with each asset. Remember, risks come in many forms, from password practices and data storage to third-party vendors and natural disasters. Even employee or client mistakes should be considered a risk. Brainstorming with employees across all parts of the firm will help identify as many potential threats as possible.With assets and risks identified, consider what cybersecurity efforts are necessary to enact safeguards. The framework core suggests categorizing activities and objectives by five functions: identify, protect, detect, respond and recover.
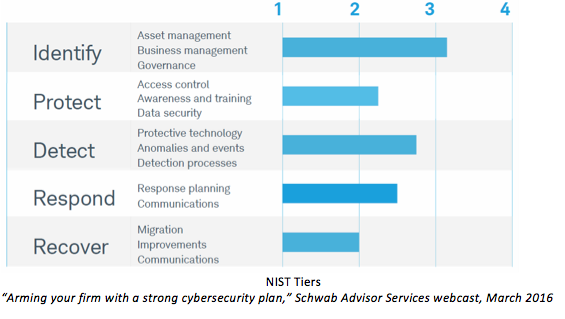
Developing the initial framework is no small task, but firms with this process in place are in a strong position for interacting with auditors and vendors.
Phase II: Keeping Pace With A Changing Business Environment
Think of security as an evolving part of the business. It should change along with technology and along with the firm. Advisors must be able to demonstrate to regulators a process for monitoring and evaluating controls in a certain area even if that process is not yet fully mature.
Framework implementation tiers provide a guide for scoring the strength of controls relative to best practices. The NIST tiers span four levels, from “partial” to “adaptive,” and provide a useful tool for demonstrating a plan to stakeholders or to an auditor.
Phase III: Profile For Success
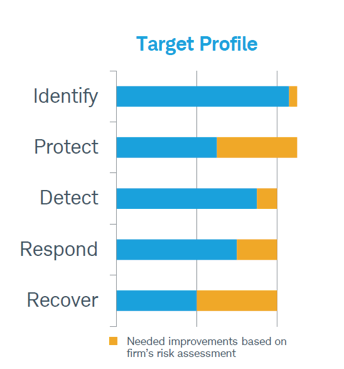
Finally, the framework profile is a scorecard for evaluating the state of play. It allows a firm to benchmark its present state relative to its “target profile.” The target profile describes what the firm plans to do to better strengthen its information security practices, technical and operational infrastructure, and physical environment. Based upon considerations such as whether there are multiple layers of control at every level, where the biggest vulnerabilities lie and which residual risks could be being overlooked, the profiles become points on a timeline, against which progress can be measured over the lifetime of the plan.
Implement And Document
The completed framework profile and target profile puts a firm in position to create an action plan. Allowing for incremental improvement, the plan should include training activities, implementation of new controls and processes for ongoing monitoring, testing and self-auditing.
Audits should be done at least annually to ensure the plan is on track. Third-party audits and other vulnerability tests can be useful for exposing deficiencies. The plan should also define a process for collecting, analyzing metrics and providing regular updates to firm leaders to inform them of progress, risks and challenges to completing the action plan.
Keep in mind that documentation will be critical and is typically one of the first pieces of information requested by auditors and regulators. Documentation of everything from training activities, to self-audits and new controls will serve as valuable evidence in the event of a regulatory inquiry.
There is no one size fits all approach to cybersecurity and building a program is not a one-and-done event. Any plan should be dynamic and able to evolve within its framework to adapt to changes in the business, the regulatory environment and trends in cybercrime. Finally, remember that while creating a solid plan is essential, it’s not just about putting the plan on paper. A program will only be effective if it is consistently implemented by employees on a daily basis. Creating a culture of protection where every member of the team is aware and committed to doing their part to protect firm and client assets is the ultimate way to protect your firm from cyber threats.
Nick Georgis is senior vice president of Schwab Advisor Services.