Phase I: Taking Stock
The foundation of the NIST approach is the framework core, which involves taking a comprehensive inventory of assets that must be safeguarded, along with existing controls that protect them. The inventory should include a firm’s hardware, software, data and intellectual property, and client information. It should also involve “directional” inventory, which includes firm-wide business strategy and future technological needs. The inventory should then be ranked by importance.
Next, identify risks associated with each asset. Remember, risks come in many forms, from password practices and data storage to third-party vendors and natural disasters. Even employee or client mistakes should be considered a risk. Brainstorming with employees across all parts of the firm will help identify as many potential threats as possible.With assets and risks identified, consider what cybersecurity efforts are necessary to enact safeguards. The framework core suggests categorizing activities and objectives by five functions: identify, protect, detect, respond and recover.
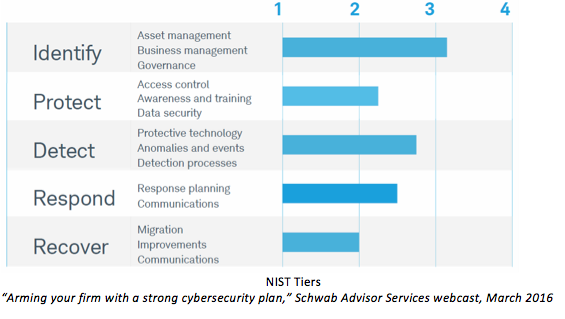
Developing the initial framework is no small task, but firms with this process in place are in a strong position for interacting with auditors and vendors.
Phase II: Keeping Pace With A Changing Business Environment
Think of security as an evolving part of the business. It should change along with technology and along with the firm. Advisors must be able to demonstrate to regulators a process for monitoring and evaluating controls in a certain area even if that process is not yet fully mature.
Framework implementation tiers provide a guide for scoring the strength of controls relative to best practices. The NIST tiers span four levels, from “partial” to “adaptive,” and provide a useful tool for demonstrating a plan to stakeholders or to an auditor.








